Decoy credentials are a powerful tool in a deception team’s toolbelt because attackers love stealing credentials to further their attack. While different sources report differing percentages, research (1, 2, 3) indicates that stolen credentials account for up to 35% of initial compromises, and are found in some way in up to 77% of attacks. This post will explore ways defenders can exploit attackers’ reliance on stolen credentials to catch them more quickly.
Permanent Amazon Web Services (AWS) Application Programming Interface (API) decoy key
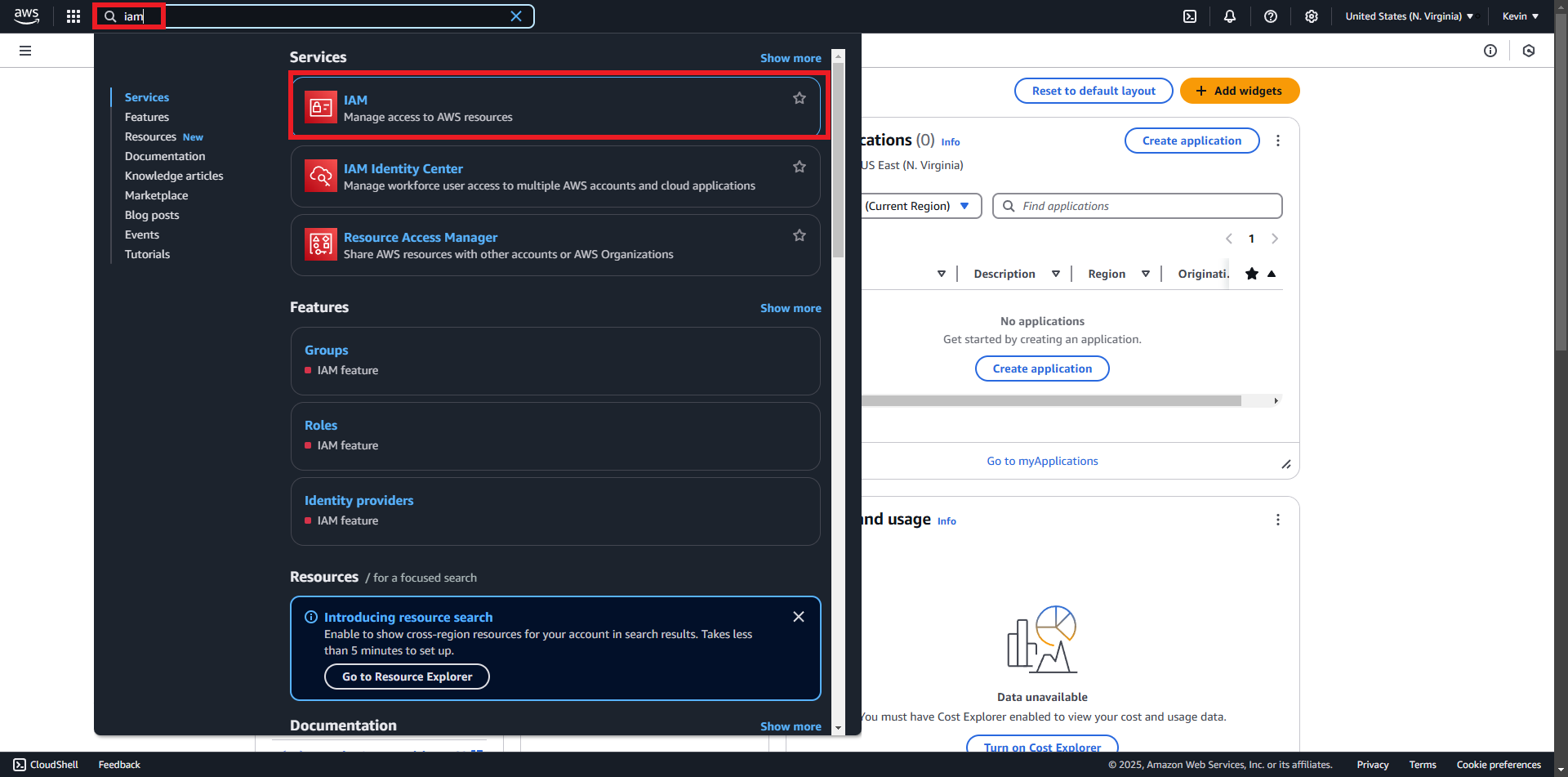
Permanent AWS API keys can be created using the IAM service. Permanent access key IDs start with the prefix AKIA, followed by the rest of the key content. In order to create a permanent API key, follow the steps below in the AWS console:
- Search for the IAM service and “IAM”
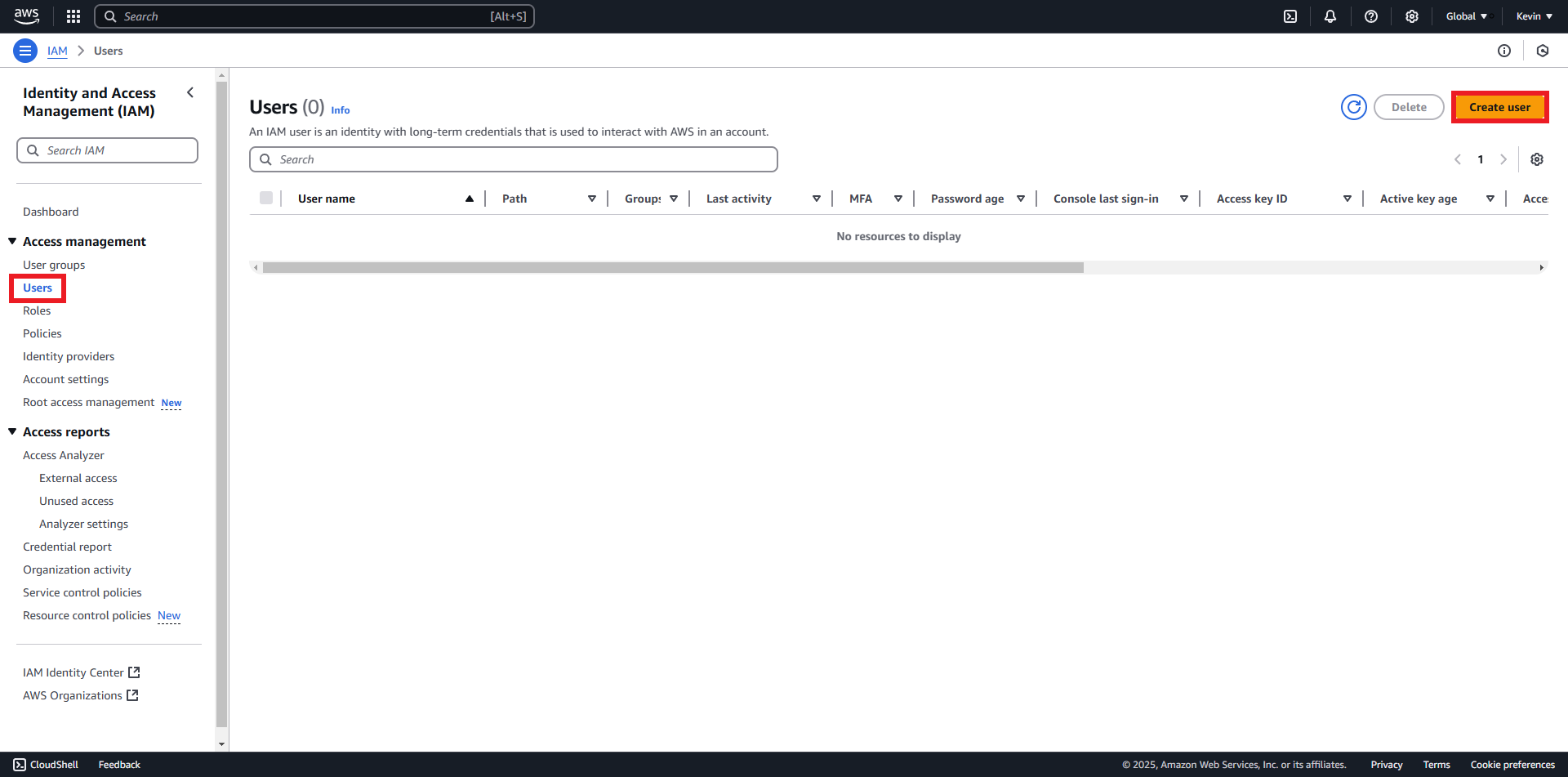
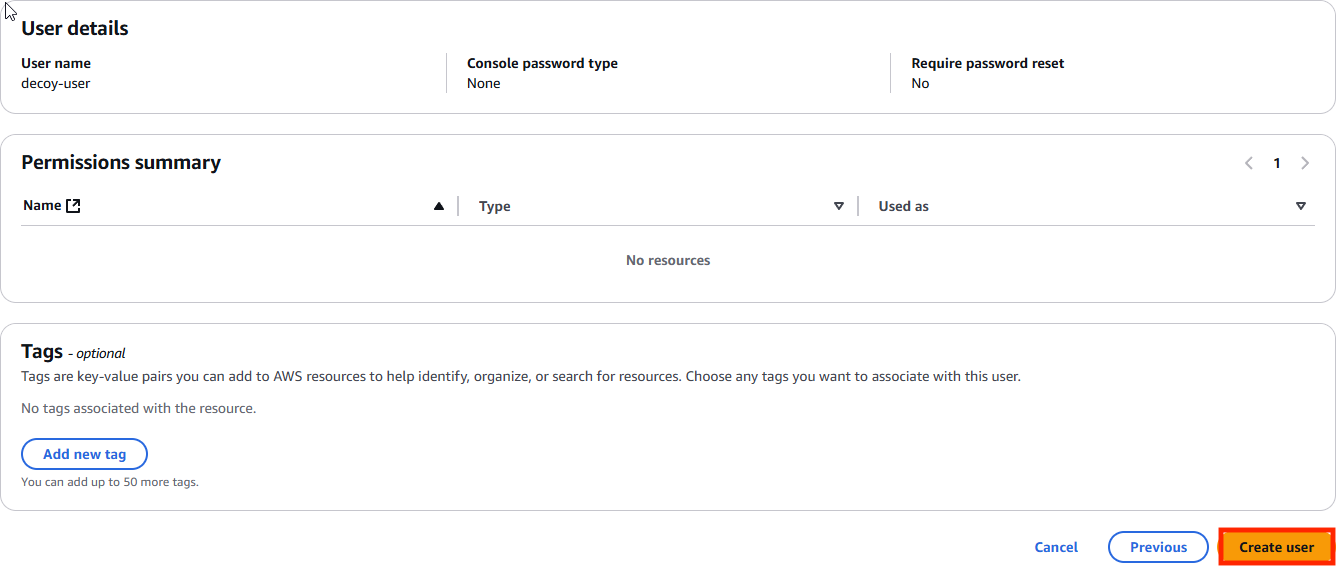
- Click “Users” » “Create User”
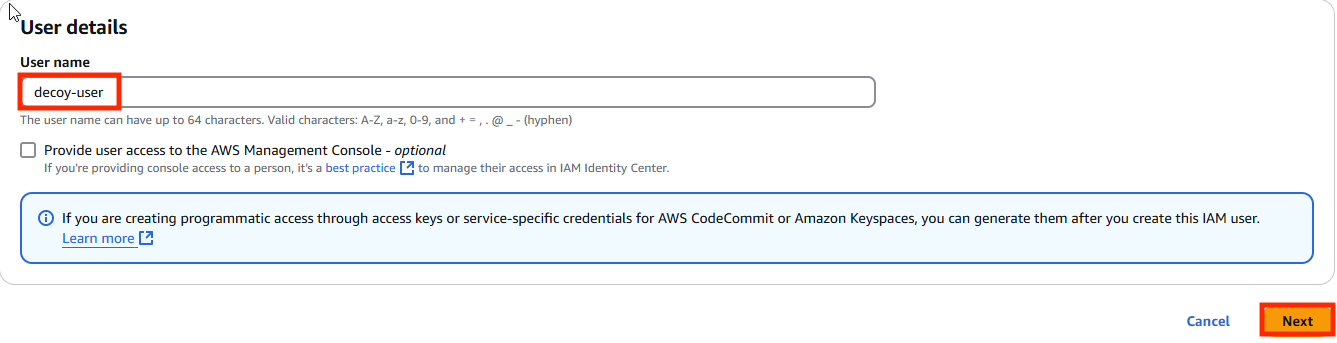
- Enter desired name and click “Next”
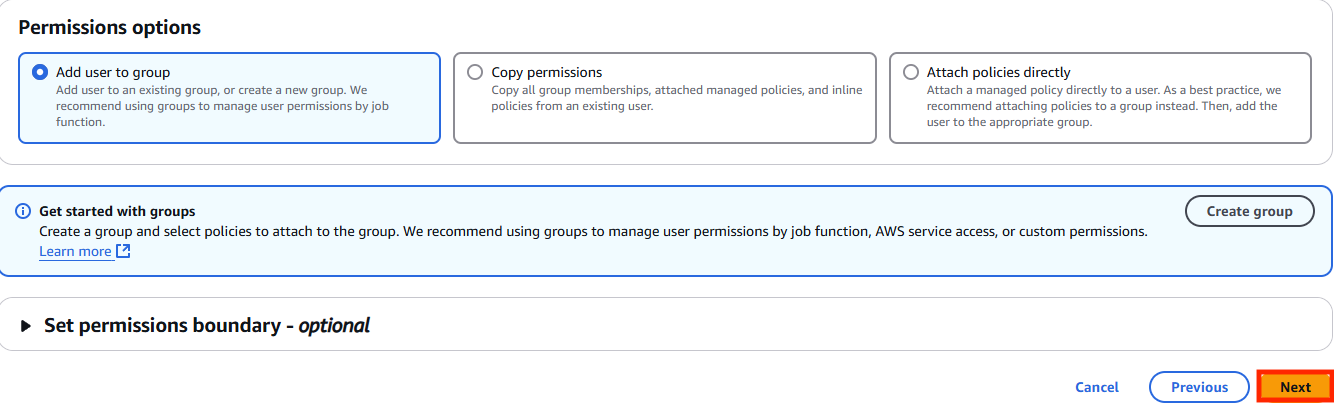
- Click “Next”
- Click “Create User”
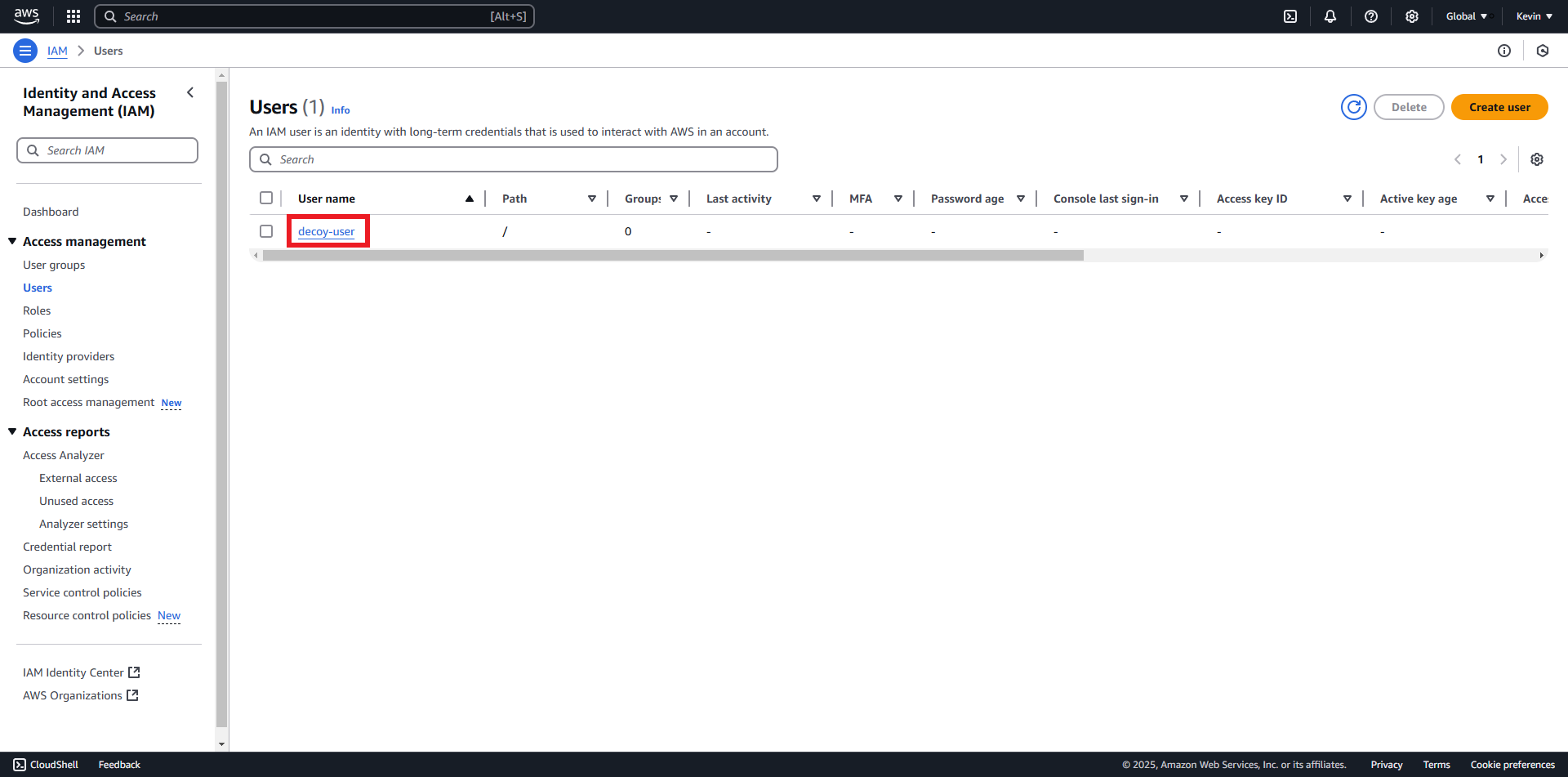
- Click on the created user
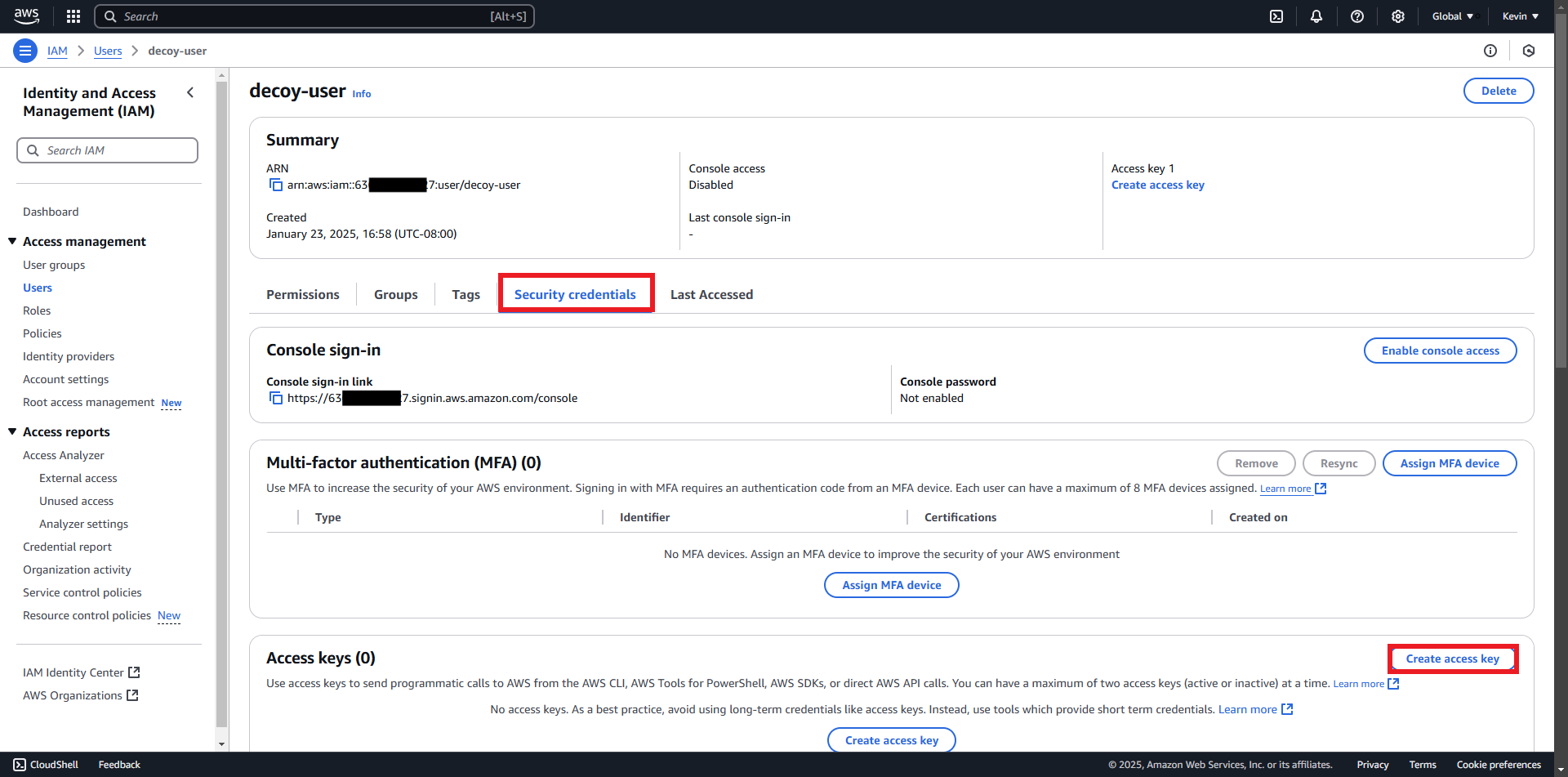
- Click “Security Credentials” » “Create Access Key”
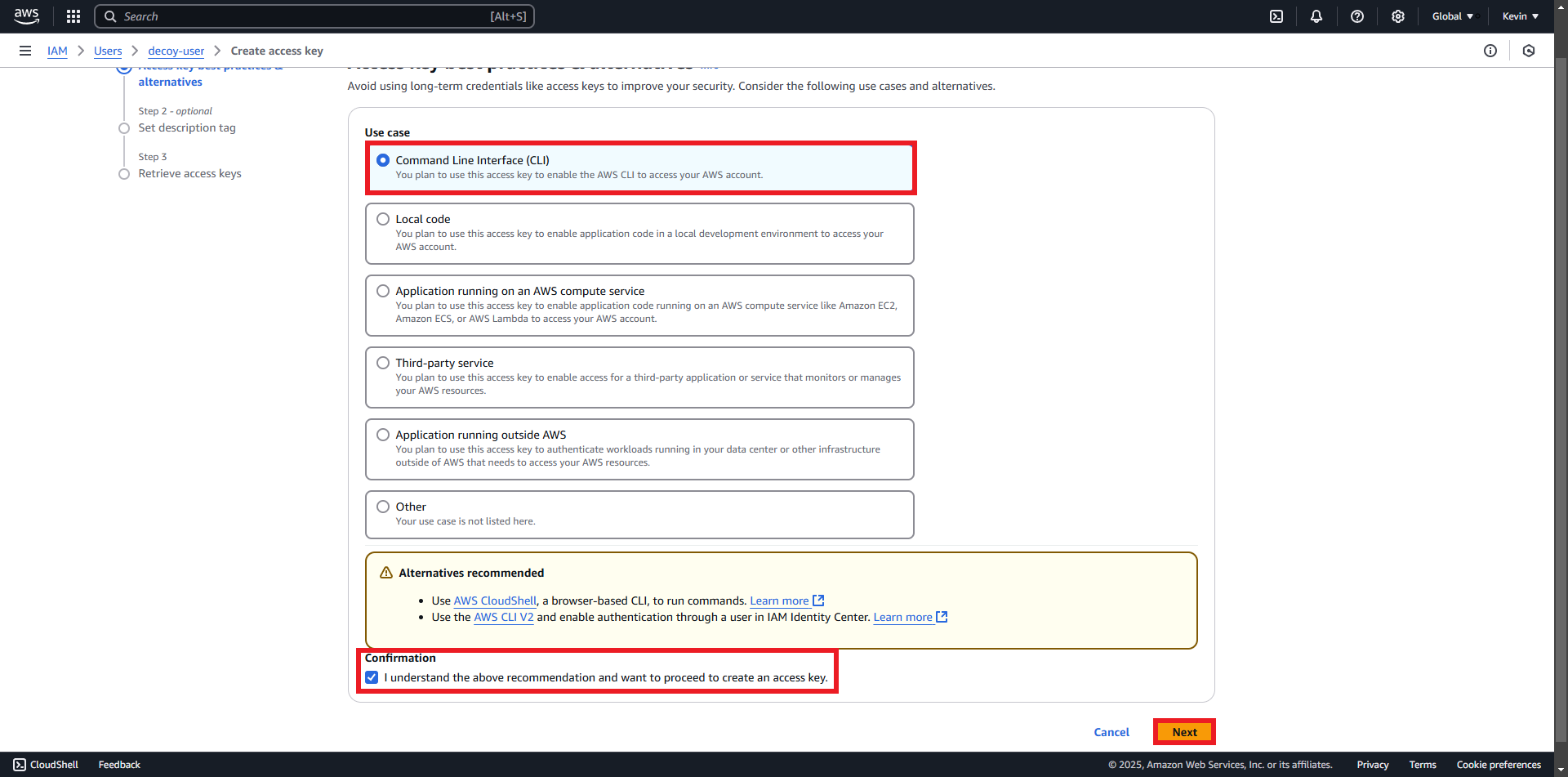
- Check “Command Line Interface” » “I understand…” » “Next”