Unlike decoy machines discussed in the last post, decoy files cannot always be created as primitive decoys. Cloud native decoy files, like Google Docs, can be primitive decoys. Decoy files made with offline text editing software, like Microsoft Word, cannot be; in order to alert a security team that an attacker has opened an offline decoy file, the file must contain a primitive decoy like a domain name or an internet-hosted image. If a security team believes that most attackers who compromise its file hosting service will open documents in that service, it is best to use the native file format with its scripting capabilities as decoys. If the team believes that attackers will download files and inspect them offline, it is better to create decoy files in the file editing software of choice and store them in the hosting service. This post will examine the two scenarios, explain how to create the different types of decoys, and demonstrate how they work.
A Google Doc decoy
Many file hosting services - for example, Google Drive - have custom file types that closely mimic the types of files users are familiar with from their own computers. In Google Drive’s case, a Google Doc is similar to a Microsoft Word document, Google Sheets is similar to Microsoft Excel spreadsheets, and Google Slides is similar to Microsoft Powerpoint slide decks. Although files can often be seamlessly converted from one to the other and back, the two are different, and therefore work differently behind the scenes. One of the many differences between a Google Doc and a Microsoft Word document is the way scripts (or in the Microsoft dialect, “macros”) work. A document can have an associated Apps Script, written in Javascript, that runs a program. To create a sample decoy using Google’s Apps Script, open a new Google Doc, then:
- Click “Extensions” » “Apps Script”
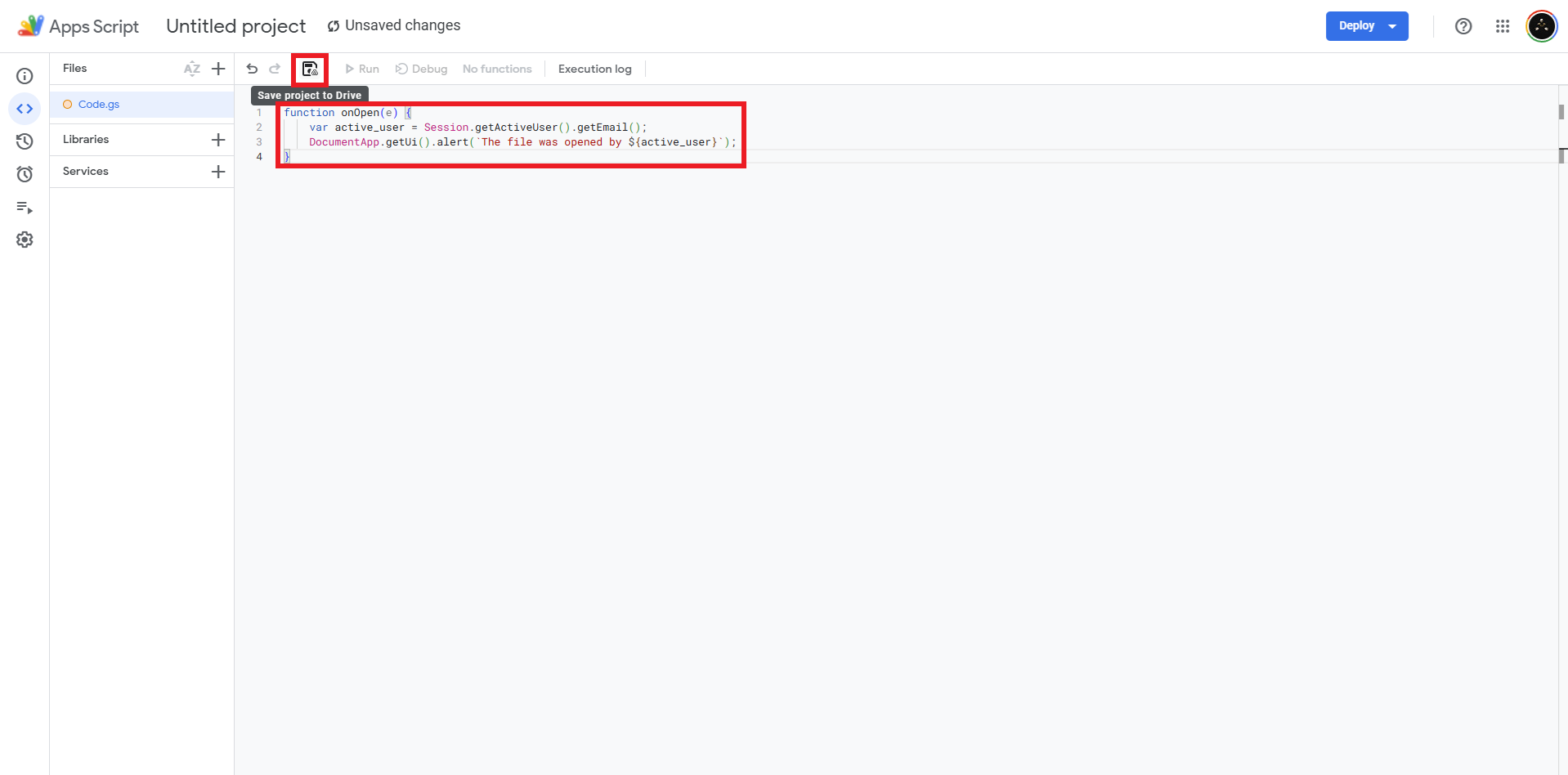
- Enter the following code and save the script
function onOpen(e) {
var active_user = Session.getActiveUser().getEmail();
DocumentApp.getUi().alert(`The file was opened by ${active_user}`);
}