Every organization has a finite amount of resources it can dedicate towards protecting itself; in order for a deception program to make sense, it has to produce a greater improvement in the organization’s security posture than any alternatives of equal cost. Investments in Information Security typically aim to do one of two things:
-
Prevent attackers from succeeding by placing obstacles in their path.
-
Detect an attacker’s presence so defenders can remove them.
Consider the types of investment through the lens of a medieval castle (modern day organization) defending itself from thieves (modern day attackers). A castle’s existence begins as walls built around a space deemed valuable; without the walls, thieves could easily walk through the space and help themselves to its valuables. With protective walls in place, A thief’s only option is to enter and exit through the walls - either through existing doors or holes they discover or create. Walls, though a necessary first investment, are more effective with guards posted at every opening. Guards can prevent known-bad individuals from bypassing the walls and inspect suspicious individuals’ items before they leave to ensure they haven’t taken any of the valuables. When starting a new castle, it is hard to argue against the first two investments of walls and guards.
Because modern day problems require modern day solutions, today’s organizations often protect their networks with walls of fire, their computers with antivirus, and their accounts with passwords. These are the modern day equivalents of a medieval castle’s basic wall, as they build a perimeter around a virtual space. After that, organizations usually employ or contract professionals that perform Security Operations Center (SOC) duties; these are the 21st century’s guards.
It’s hard to decide what to invest in next once a castle’s walls are built and guards are trained. The possibilities are nearly endless: make the walls higher, make the walls thicker, reinforce the walls with stronger material, build a moat, replace the moat entrance with a drawbridge, fill the moat with predators, train more guards, train the guards better, give the guards better tools, train all of the castle’s inhabitants in some way, build a vault inside the castle, or some other solution not listed here. There is likely no one-size-fits-all-castles answer because every castle will have different valuables to protect, encounter different types of thieves, have different tolerances for risk, have different budgets, and define different criteria for success.

In securing a modern day organization, there are equally many choices. Segmenting a network by sensitivity or purpose, hardening the operating system its machines use, enforcing multi factor authentication (MFA) on accounts and logins, training end users to identify and avoid suspicious links and attachments, filtering email from unknown sources, deploying endpoint detection and response (EDR) agents, limiting who can install software, and deploying deception are just a few of the many common practices. While there is no easy way to determine which investment will be best, deception’s advantages make it a great choice for some environments.
Flexibility
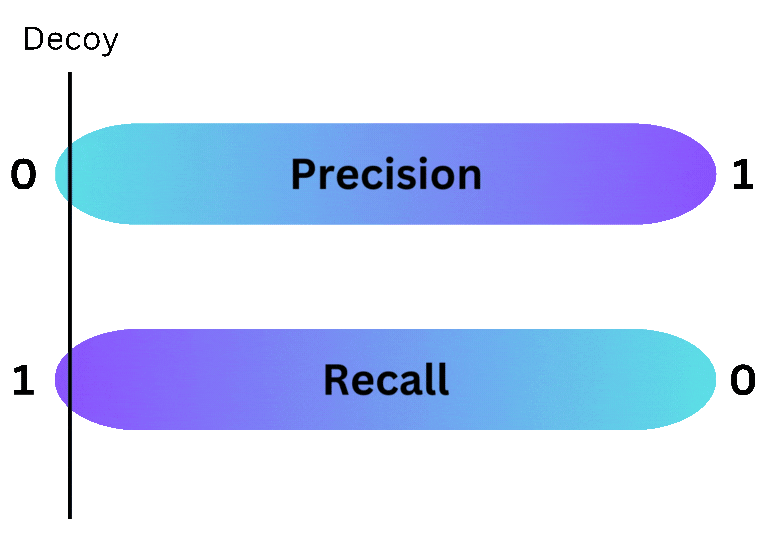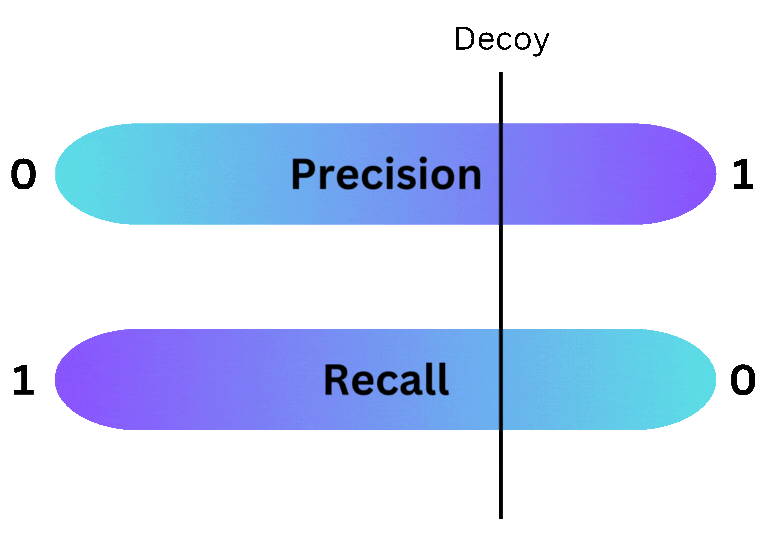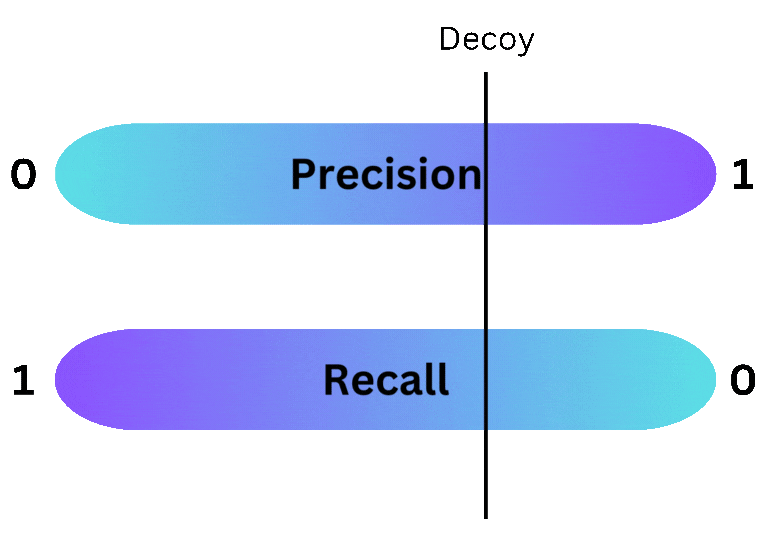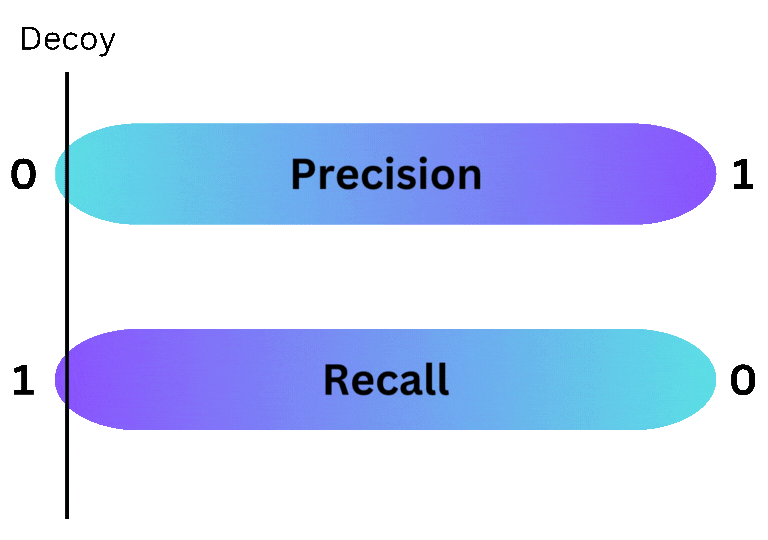
Deception provides more flexibility to the security team deploying it than traditional security tools. While all security tools are subject to the same unfortunate truth - increasing the precision of a tool decreases its recall (and visa versa) - deception allows a security team to choose exactly where a given decoy lands on the precision/recall spectrum. By placing decoys in commonly searched places, defenders can reduce the number of evaded alerts, increasing recall. Alternatively, by hiding decoys in less common areas, defenders can reduce benign positive alerts, which increases precision. This flexibility makes deception a great choice for organizations that want to fine tune the fidelity of the alerts they receive.
Performance impacts
Decoys usually impact the performance of the systems they run on much less than traditional security tools. For example, to protect an employee’s workstation, an organization might use an EDR that monitors running processes, files reads and writes, network connections, and other activity on the workstation. While EDRs protect workstations and detect malicious actions on them well, they consume a portion of the workstation’s limited resources (RAM and CPU in particular) in order to do so. In contrast, decoys placed on a workstation in order to protect it often consume no resources unless something interacts with it, which should not happen under normal circumstances.
As another example, protecting a network may involve the use of an intrusion prevention system (IPS) or a next-gen firewall (NGFW) that records and monitors network traffic. Depending on the size of the network, this can be a very computationally expensive endeavor and may impact the performance of the network. A few strategically placed decoy machines may alert an organization to the presence of a malicious actor with almost no added overhead. Because deception is able to protect an environment without straining its resources, it can be a great choice for environments that cannot tolerate the performance impacts of traditional security tooling.
Resiliency
Decoys are often less susceptible to subtle changes in attacker tradecraft than traditional security tools. The classic example of defeating antivirus of the past (and unfortunately sometimes the present) is an attacker who changes the hash of their malware. By changing the name of a variable, adding an irrelevant line of code, or swapping the order of two instructions, an attacker could alter the hash of their malware’s executable, which would defeat antivirus systems that rely on detecting known-bad hashes. While advancements in endpoint detection render changing a hash far less effective, most traditional security tools rely on identifying common patterns that one or more pieces of malware use in order to achieve its goal. If a malware developer discovers a previously unknown technique that accomplishes the same outcome or finds a way to prevent the EDR from gathering the required data to detect the malicious activity, it will likely be able to evade detection until EDR vendors update their products to catch the new technique.
Decoys, on the other hand, target what an attacker wants, like credentials, privileged accounts, and sensitive files, rather than what they do to get it, like reading memory, enumerating account permissions, and reading files. Well-designed decoys look like the valuable an attacker is after, whether that is: information useful for internal reconnaissance, a path for lateral movement, or a way to perform privilege escalation. Using deception is like transforming a guard into one of the gold bars in a castle’s treasure - if a thief steals a castle’s treasure, they are likely to “steal” its deception as well. A traditional security tool’s approach of posting guards near the vault that holds a castle’s treasure will likely catch many thieves, but skilled or lucky ones who take a novel approach to the treasure will go undetected.


Cost
Decoys can be a much cheaper alternative to traditional security tools. Licensing an EDR, IPS, NGFW, or other traditional security product can be prohibitively expensive for organizations with large fleets compared to their budget for security. While a mature security program will complement the aforementioned tools with deception, deception may offer a relatively inexpensive boost to a security landscape.